Technology Tips: June 2021 Edition

|
Skyward IT Services Network and Infrastructure Security Specialists |
A look into the Colonial Pipeline ransomware attack
If you think password security is over-hyped, you may want to think again. One stolen password was all it took for the Colonial Pipeline to get hacked by cyber-criminal group DarkSide last month. Hackers threatened to shut down the 5,500-mile pipeline with a ransom of nearly $5 million.Colonial Pipeline Chief Executive Joseph Blount told the U.S. Senate committee that hackers used a legacy VPN which didn’t have MFA (multifactor authentication) in place. Fortunately, 60 out of 75 of the Bitcoin paid as ransom were recovered, but their value has dropped since the initial attack.
If there is a lesson to be learned from this unfortunate event, it’s that it is more important than ever to make sure your data security practices are in tip-top shape before a crisis arises. Here are some great resources on password protection, MFA, and data security for your district.
Calling out hackers
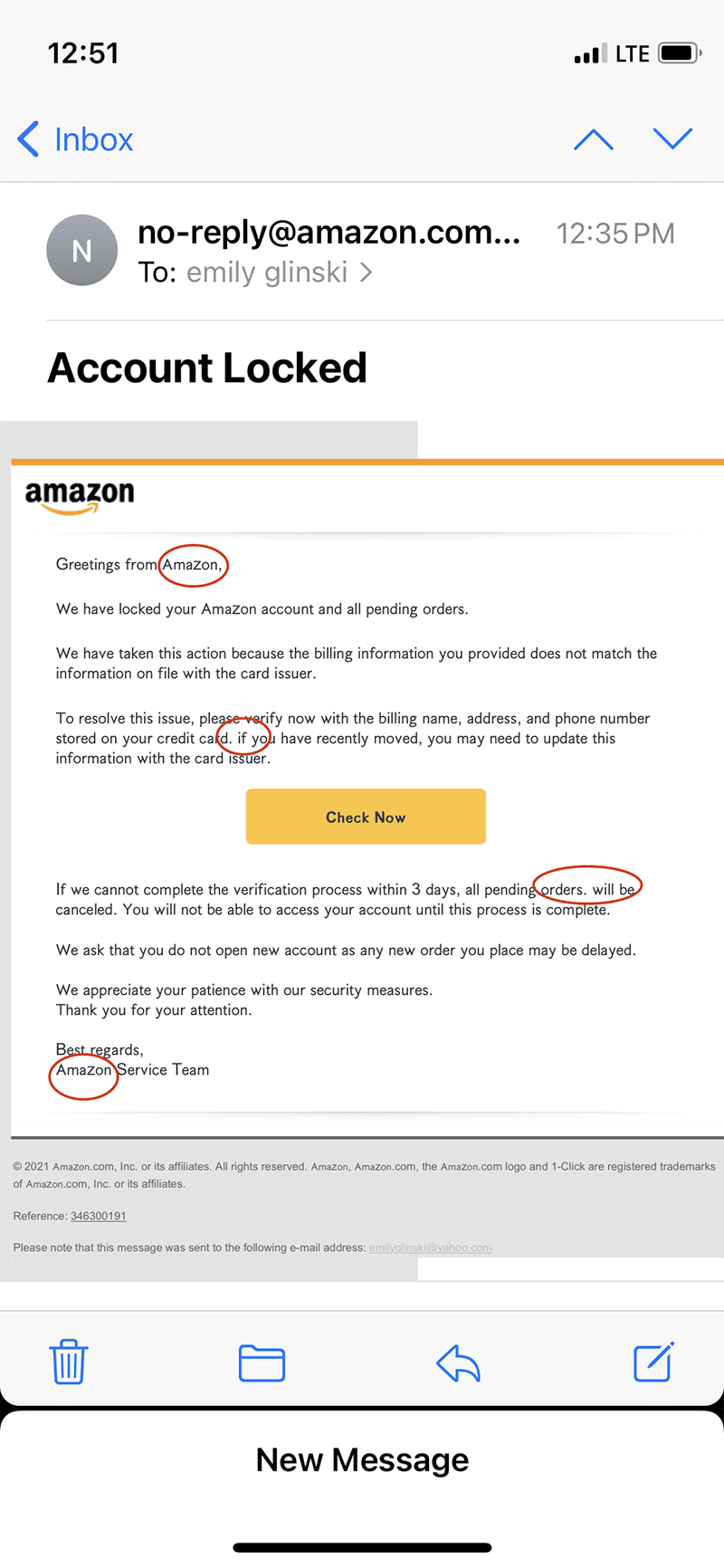
You’ve likely received dozens (possibly hundreds) of emails from hackers without even realizing it. Let’s take a look at this seemingly harmless email from Amazon, for example. What red flags do you see?
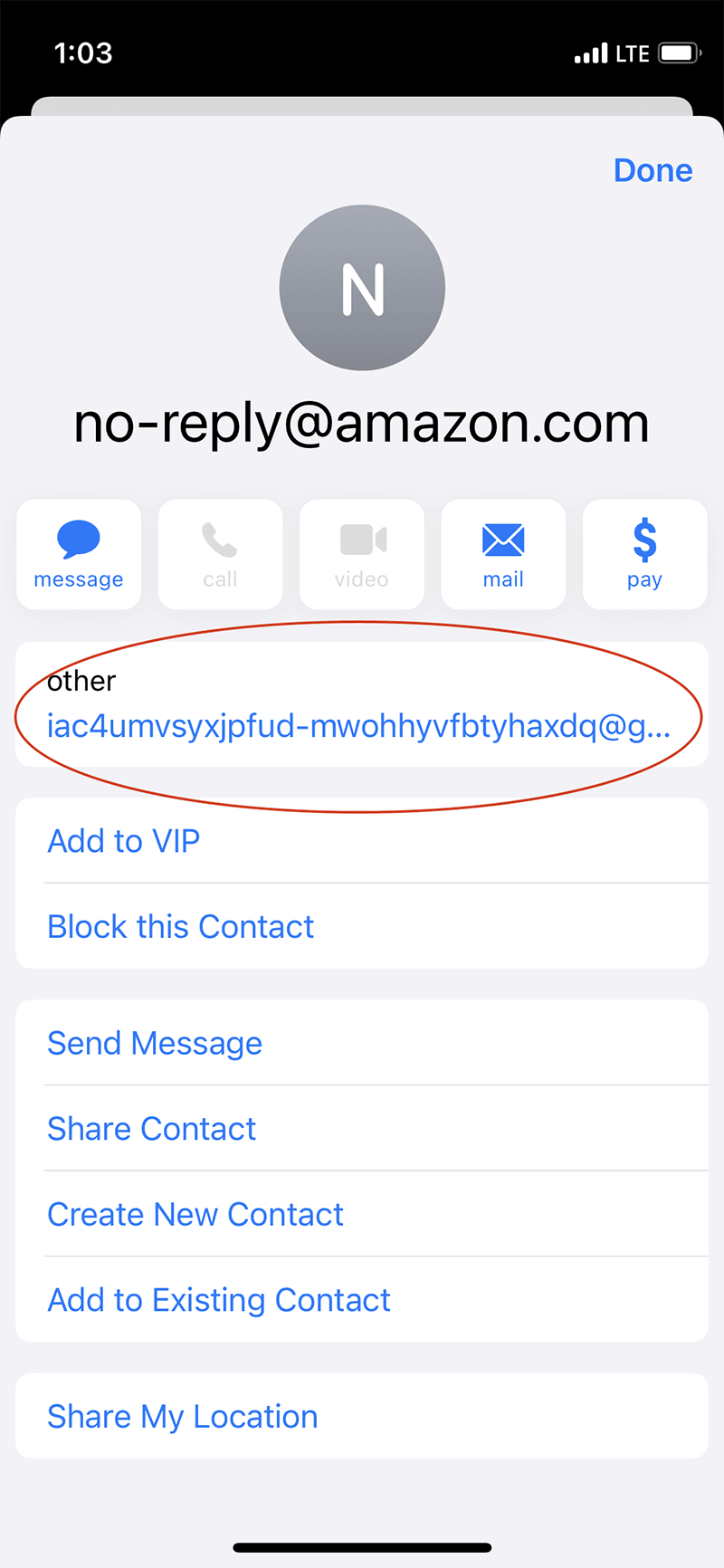
The sender’s email “no-reply@amazon.com" appears to be valid, as well as the logo and colors throughout the email. But take a closer look, and you can see numerous (though subtle) errors.
You'll notice punctuation errors and the spelling of “AmaZon” throughout the email. When clicking on the sender email account, the email address (the long string of text labeled "other") is certainly not legitimate. (By the way, it’s okay to leave this to the IT pros to investigate—don’t click unless you’re confident a link won’t compromise your systems and networks!)
Always make sure to scan through every email before clicking on a link. If you do click, it can allow hackers to install malware on your device. Hackers rely on urgency and will often lie about the status of your credit cards, bank account, and other accounts.
Another way hackers attack is via phone calls. Over the past few years you may have received a variety of urgent phone calls.
“You owe a large sum of money, and the IRS/authorities have been notified.”
“Your grandson is in jail and needs $___ for bail immediately.”
“This is the IRS. Please confirm your routing number so we can deposit your stimulus check.”
Such calls are from the workings of hackers, and they tend to prey on older individuals. You can never be too cautious with suspicious calls and emails. When in doubt, reach out directly to your bank, the IRS, etc. via the contact information you have on file or find on their website. Then ask them to verify they are trying to contact you. If you think you’ve received scams or are the victim of fraud, you can report them here.
Smart Device Malware
It’s all fun and games until a hacker burns your coffee.Most of us are well aware of the basics of data security when it comes to our devices.
But what about unsuspecting objects like smart coffee makers and DSLR cameras? Hackers have found numerous ways to crack into our cell phones and computers by breaking into the Internet of Things, those at-home devices that use our wi-fi.
A smart coffee maker can be a convenient and tech-savvy way to get our morning cup of joe. Being able to brew and schedule our coffee from an app sounds mighty convenient… but how safe is it actually?
Hackers can do worse than burn or delay your coffee; they can use your coffee maker as a tool to install malicious code on any device that uses the same wi-fi network. One way to protect your home is to password protect the coffee maker itself, as well as the wi-fi network it is using. Make sure to change any default passwords and keep the firmware on your devices updated.
Researchers also found that Canon DSLR cameras are at risk for being hacked and used for malicious activity through the camera’s USB and wi-fi capabilities. Hackers could threaten to delete photos and video files until a ransom is paid. Canon is aware of this potential risk and issued a statement with additional information and tips on keeping your camera safe.
Malware of the month
A new malware is on the market that is 10 times more dangerous than the typical malware. Yikes. Jackware is its name, and hacking embedded devices is its game.An embedded device refers to tiny computers that are in infrastructure, cars, healthcare, homes, and office buildings. When Jackware hacks the embedded device, it can have lasting physical consequences, such as breaking a million-dollar MRI machine, office IT system, school security system, subway, or taking control of vehicles. Additional risks include disrupting processing plants, oil and gas companies, and electric and utilities.
These threats are unpredictable and can happen to any organization. That’s why it’s a good idea for the average person to prepare for an abrupt disruption by having enough supplies on hand, such as food, water, and a generator if possible.
Thinking about edtech for your district? We'd love to help. Visit skyward.com/get-started to learn more.
|
Skyward IT Services Network and Infrastructure Security Specialists |

 Get started
Get started