Pattern recognition can help keep your network and devices safer. Here are five common patterns in phishing emails that work to net credentials and help hackers slip between your defenses.
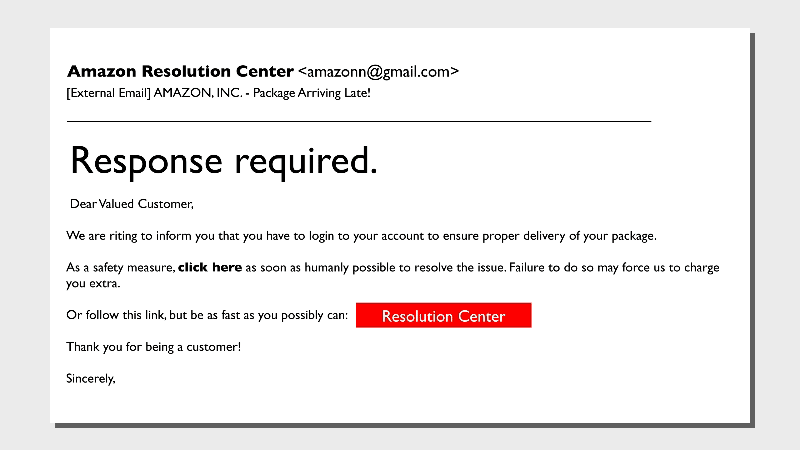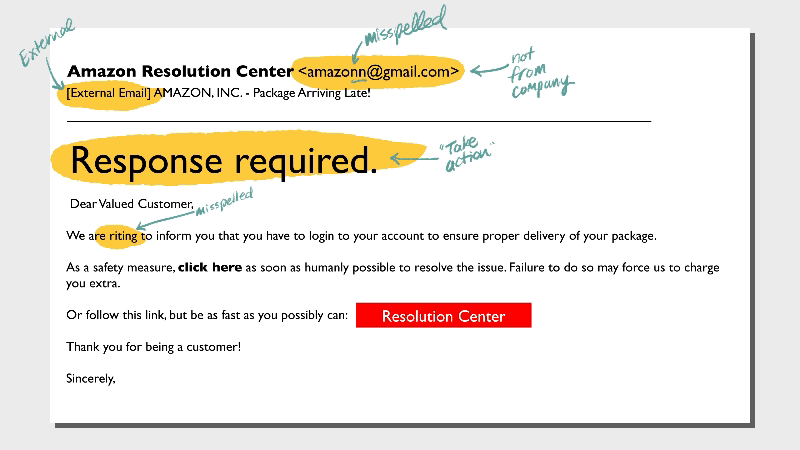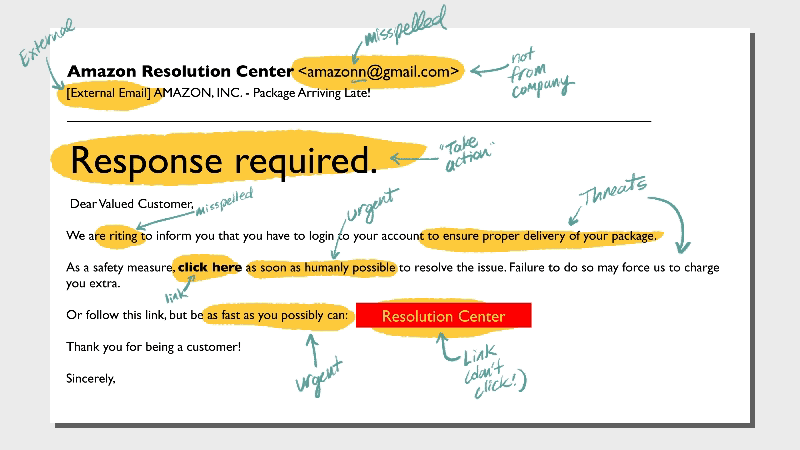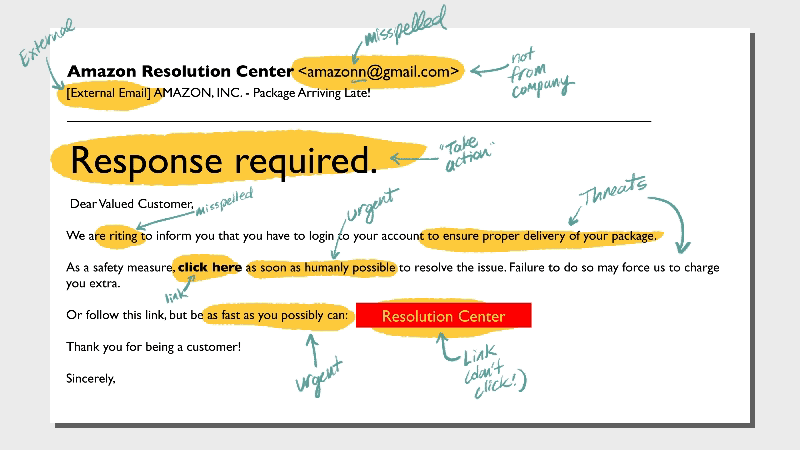
1. Mabye you splet something wrong
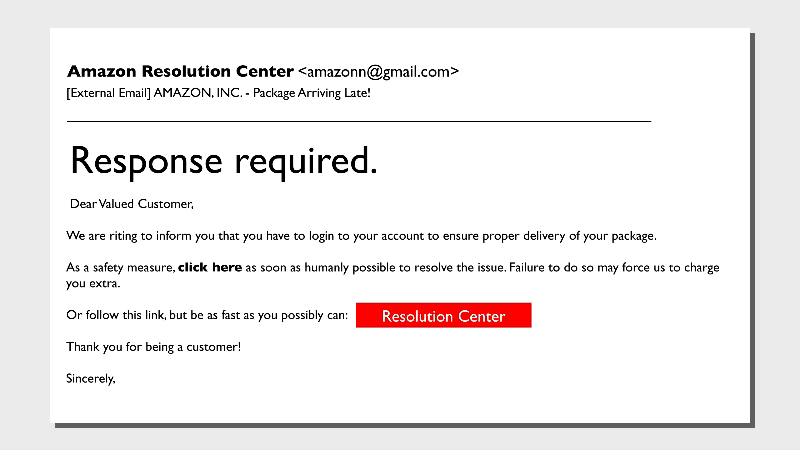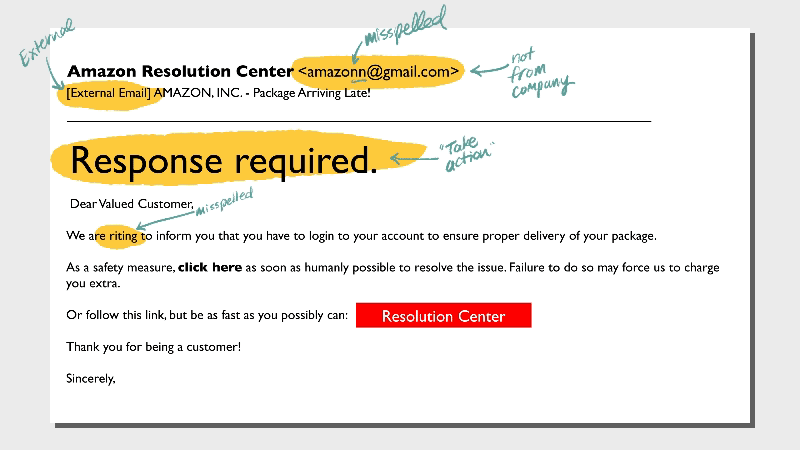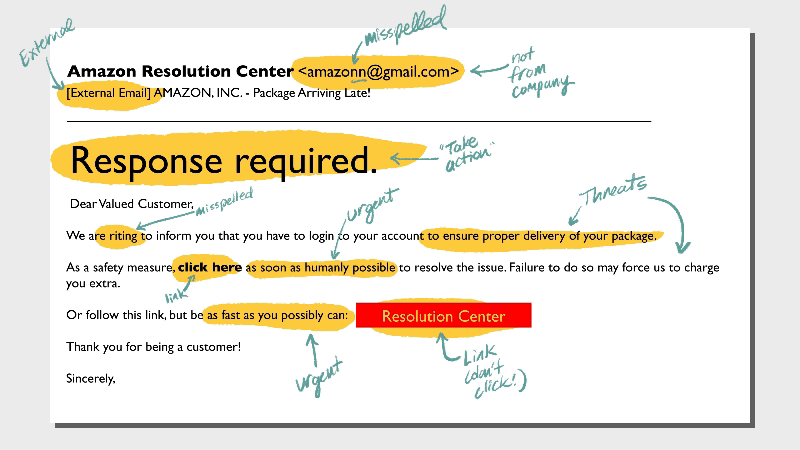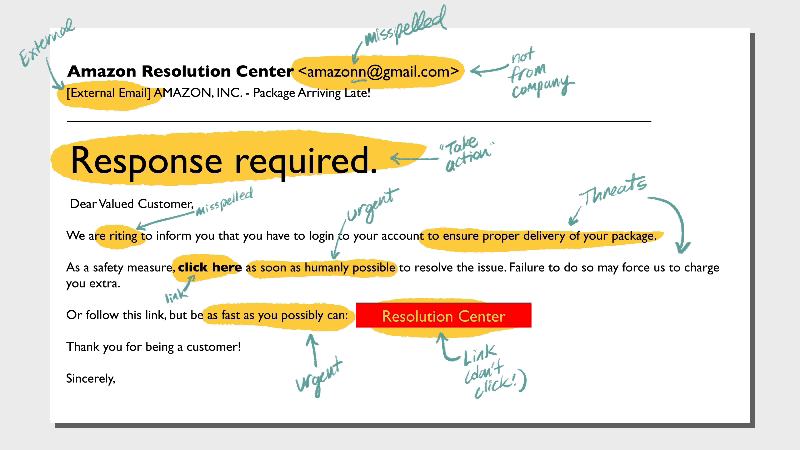
Not-quite-right language is a hallmark of phishing emails. You may find misspellings, unnecessary punctuation, and odd tone. The message may sound overly formal or somewhat archaic.Typos are one thing, but a whole email full of suspicious usage is a red flag.
What to do instead: Brush up on your typical business-related or vendor email formats and get to know them well. When something feels off, it probably is, so don’t click! Instead, report the email to your IT crew.
2. So close to the real thing
Phishing emails are designed to be compelling—hackers’ paydays depend on it. So don’t feel too bad if you’re almost tricked. Take a hard look at a few telltale signs that the note from Amazon or your bank isn’t actually from the legit vendors.- Look very closely at the email address. Is it one or two characters off?
- Is the domain name odd? For example, customerservice@amazonmembership.com reveals some redundancy that normally wouldn't show up in a business email.
- Are there logos that don’t match? Do the logos look distorted or stretched?
Be extra careful with plain text emails, especially if they’re unsolicited and feel like they should be fancy HTML designed. Any email from a vendor should also include a link to unsubscribe, view a privacy policy, and copyright info. If that boilerplate info is missing, it’s suspicious.
What to do instead: If you’re concerned about your account but want to avoid a phishing mishap, go to the real website and use your credentials to log in; don’t log in through the email.
3. Sneaky links and attachments
The whole point of the phishing email is to get you to take action. This trickery usually comes in the form of links or attachments.NEVER open an attachment from someone you don’t know. Even opening the file can release malicious software into your machine and network. When it’s a link, hover over it to read the entire destination, since some links are embedded in the body text. Some redirects (extra stuff after the domain name) are fairly normal, like UTM codes which are used to track marketing activity. For the most part, be suspicious of these types of long URLs. It’s just not worth the risk, especially if it sounds too good to be true.
What to do instead: Don’t click on a link! Instead, follow up on the topic with the sender or quench your unwavering curiosity with a Google search accompanied by “scam?” (And if you have to ask, it probably is.)
4. Beware name droppers
Social engineering pays off for most hackers, and when you think about it, it’s fairly easy to do thanks to access to LinkedIn, school website directories, and personal social media accounts. It never hurts to check in IRL when something seems phishy in cyberspace, especially when the email claims to be an administrator asking for funds, gift cards, or other perks last-minute. Even the crabbiest supervisor will appreciate your diligence to keep their personal data secure.Speaking of supervisors, if you’re in a position of authority, be consistent in communication and ensure your direct reports know your routines. That way they can easily spot someone pretending to be you.
What to do instead: Pick up the phone and call the person to confirm they were indeed the one who sent the email and always use approved processes for transferring funds.
5. Threats
Whether the message comes via text, email, or some other way, threats are always a red flag that hackers are behind it, not customer service representatives. Real government agencies and businesses do not threaten their customers—at least not by unsolicited email.What to do instead: Don’t be intimidated by criminals’ empty threats. Contact your local law enforcement to report these kinds of scams—you might know better than to fall for them, but lots of your neighbors need help.
One of the best exercises you can practice as a human firewall is to get familiar with the tried-and-true tricks hackers use to hit their jackpots. The bad guys won’t slow down, but we can catch on to their methods.
WHAT'S NEXT FOR YOUR EDTECH? The right combo of tools & support retains staff and serves students better. We'd love to help. Visit skyward.com/get-started to learn more.

|
Erin Werra Blogger, Researcher, and Edvocate |
Erin Werra is a content writer and strategist at Skyward’s Advancing K12 blog. Her writing about K12 edtech, data, security, social-emotional learning, and leadership has appeared in THE Journal, District Administration, eSchool News, and more. She enjoys puzzling over details to make K12 edtech info accessible for all. Outside of edtech, she’s waxing poetic about motherhood, personality traits, and self-growth.